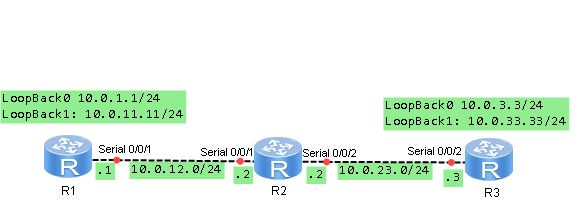
1. Cihaz isim ve Ip address yapılandırması.
<Huawei>system-viewEnter system view, return user view with Ctrl+Z.[Huawei]sysname CLIGURU-R1[CLIGURU-R1]interface serial 0/0/1[CLIGURU-R1-Serial0/0/1]ip address 10.0.12.1 24[CLIGURU-R1-Serial0/0/1]interface LoopBack 0[CLIGURU-R1-LoopBack0]ip address 10.0.1.1 24[CLIGURU-R1]interface loopback 1[CLIGURU-R1-LoopBack1]ip address 10.0.11.11 24 |
<Huawei>system-viewEnter system view, return user view with Ctrl+Z.[Huawei]sysname CLIGURU-R2[CLIGURU-R2]interface serial 0/0/1[CLIGURU-R2-Serial0/0/1]ip address 10.0.12.2 24[CLIGURU-R2-Serial0/0/1]interface serial 0/0/2[CLIGURU-R2-Serial0/0/2]ip address 10.0.23.2 24[CLIGURU-R2-Serial0/0/2]interface LoopBack0[CLIGURU-R2-LoopBack0]ip address 10.0.2.2 24 |
<Huawei>system-viewEnter system view, return user view with Ctrl+Z.[Huawei]sysname CLIGURU-R3[CLIGURU-R3]interface serial 0/0/2[CLIGURU-R3-Serial0/0/2]ip address 10.0.23.3 24[CLIGURU-R3-Serial0/0/2]interface loopback 0[CLIGURU-R3-LoopBack0]ip address 10.0.3.3 24[CLIGURU-R3]interface loopback 1[CLIGURU-R3-LoopBack1]ip address 10.0.33.33 24 |
2. OSPF yapılandırması.
[CLIGURU-R1]ospf router-id 10.0.1.1[CLIGURU-R1-ospf-1]area 0[CLIGURU-R1-ospf-1-area-0.0.0.0]network 10.0.12.0 0.0.0.255[CLIGURU-R1-ospf-1-area-0.0.0.0]network 10.0.1.0 0.0.0.255[CLIGURU-R1-ospf-1-area-0.0.0.0]network 10.0.11.0 0.0.0.255 |
[CLIGURU-R2]ospf router-id 10.0.2.2[CLIGURU-R2-ospf-1]area 0[CLIGURU-R2-ospf-1-area-0.0.0.0]network 10.0.2.0 0.0.0.255[CLIGURU-R2-ospf-1-area-0.0.0.0]network 10.0.12.0 0.0.0.255[CLIGURU-R2-ospf-1-area-0.0.0.0]network 10.0.23.0 0.0.0.255 |
[CLIGURU-R3]ospf router-id 10.0.3.3[CLIGURU-R3-ospf-1]area 0[CLIGURU-R3-ospf-1-area-0.0.0.0]network 10.0.23.0 0.0.0.255[CLIGURU-R3-ospf-1-area-0.0.0.0]network 10.0.3.0 0.0.0.255[CLIGURU-R3-ospf-1-area-0.0.0.0]network 10.0.33.0 0.0.0.255 |
OSPF komşuluklarının kurulduğunu kontrol edelim.
[CLIGURU-R2]display ospf peer briefOSPF Process 1 with Router ID 10.0.2.2Peer Statistic Information—————————————————————————-Area Id Interface Neighbor id State0.0.0.0 Serial0/0/1 10.0.1.1 Full0.0.0.0 Serial0/0/2 10.0.3.3 Full—————————————————————————- |
[CLIGURU-R1]display ip routing-tableRoute Flags: R – relay, D – download to fib——————————————————————————Routing Tables: PublicDestinations : 13 Routes : 13Destination/Mask Proto Pre Cost Flags NextHop Interface10.0.1.0/24 Direct 0 0 D 10.0.1.1 LoopBack010.0.1.1/32 Direct 0 0 D 127.0.0.1 LoopBack010.0.2.2/32 OSPF 10 1562 D 10.0.12.2 Serial0/0/110.0.3.3/32 OSPF 10 3124 D 10.0.12.2 Serial0/0/110.0.11.0/24 Direct 0 0 D 10.0.11.11 LoopBack110.0.11.11/32 Direct 0 0 D 127.0.0.1 LoopBack110.0.12.0/24 Direct 0 0 D 10.0.12.1 Serial0/0/110.0.12.1/32 Direct 0 0 D 127.0.0.1 Serial0/0/110.0.12.2/32 Direct 0 0 D 10.0.12.2 Serial0/0/110.0.23.0/24 OSPF 10 3124 D 10.0.12.2 Serial0/0/110.0.33.33/32 OSPF 10 3124 D 10.0.12.2 Serial0/0/1127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 |
[CLIGURU-R3]display ip routing-tableRoute Flags: R – relay, D – download to fib——————————————————————————Routing Tables: PublicDestinations : 13 Routes : 13Destination/Mask Proto Pre Cost Flags NextHop Interface10.0.1.1/32 OSPF 10 3124 D 10.0.23.2 Serial0/0/210.0.2.2/32 OSPF 10 1562 D 10.0.23.2 Serial0/0/210.0.3.0/24 Direct 0 0 D 10.0.3.3 LoopBack010.0.3.3/32 Direct 0 0 D 127.0.0.1 LoopBack010.0.11.11/32 OSPF 10 3124 D 10.0.23.2 Serial0/0/210.0.12.0/24 OSPF 10 3124 D 10.0.23.2 Serial0/0/210.0.23.0/24 Direct 0 0 D 10.0.23.3 Serial0/0/210.0.23.2/32 Direct 0 0 D 10.0.23.2 Serial0/0/210.0.23.3/32 Direct 0 0 D 127.0.0.1 Serial0/0/210.0.33.0/24 Direct 0 0 D 10.0.33.33 LoopBack110.0.33.33/32 Direct 0 0 D 127.0.0.1 LoopBack1127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 |
3. ACL yapılandırması.
[CLIGURU-R1]acl 3001[CLIGURU-R1-acl-adv-3001]rule 5 permit ip source 10.0.1.0 0.0.0.255 destination 10.0.3.0 0.0.0.255 |
[CLIGURU-R3]acl 3001[CLIGURU-R3-acl-adv-3001]rule 5 permit ip source 10.0.3.0 0.0.0.255 destination 10.0.1.0 0.0.0.255 |
4.IPsec VPN konfigürasyonu.
IPsec proposal oluşturmak ve kullanılacak güvenlik protokollerini belirtmek için IPsec proposal moduna girelimve ayarlarını yapılandıralım .
Cihazlarında aynı protokollerde olmasına dikkat edelim.
[CLIGURU-R1]ipsec proposal tran1[CLIGURU-R1-ipsec-proposal-tran1]esp authentication-algorithm sha1[CLIGURU-R1-ipsec-proposal-tran1]esp encryption-algorithm 3des |
[CLIGURU-R3]ipsec proposal tran1[CLIGURU-R3-ipsec-proposal-tran1]esp authentication-algorithm sha1[CLIGURU-R3-ipsec-proposal-tran1]esp encryption-algorithm 3des |
Yapılandırmanın doğruluğunu kontrol etmek için display ipsec proposal komutunu kullanalım.
<CLIGURU-R1>display ipsec proposalNumber of proposals: 1IPSec proposal name: tran1Encapsulation mode: TunnelTransform : esp-newESP protocol : Authentication SHA1-HMAC-96Encryption 3DES |
<CLIGURU-R3>display ipsec proposalNumber of proposals: 1IPSec proposal name: tran1Encapsulation mode: TunnelTransform : esp-newESP protocol : Authentication SHA1-HMAC-96Encryption 3DES |
5. IPsec Policy konfigürasyonu.
[CLIGURU-R1]ipsec policy P1 10 manual[CLIGURU-R1-ipsec-policy-manual-P1-10]security acl 3001[CLIGURU-R1-ipsec-policy-manual-P1-10]proposal tran1[CLIGURU-R1-ipsec-policy-manual-P1-10]tunnel remote 10.0.23.3[CLIGURU-R1-ipsec-policy-manual-P1-10]tunnel local 10.0.12.1[CLIGURU-R1-ipsec-policy-manual-P1-10]sa spi outbound esp 54321[CLIGURU-R1-ipsec-policy-manual-P1-10]sa spi inbound esp 12345[CLIGURU-R1-ipsec-policy-manual-P1-10]sa string-key outbound esp simple huawei[CLIGURU-R1-ipsec-policy-manual-P1-10]sa string-key inbound esp simple huawei |
[CLIGURU-R3]ipsec policy P1 10 manual[CLIGURU-R3-ipsec-policy-manual-P1-10]security acl 3001[CLIGURU-R3-ipsec-policy-manual-P1-10]proposal tran1[CLIGURU-R3-ipsec-policy-manual-P1-10]tunnel remote 10.0.12.1[CLIGURU-R3-ipsec-policy-manual-P1-10]tunnel local 10.0.23.3[CLIGURU-R3-ipsec-policy-manual-P1-10]sa spi outbound esp 12345[CLIGURU-R3-ipsec-policy-manual-P1-10]sa spi inbound esp 54321[CLIGURU-R3-ipsec-policy-manual-P1-10]sa string-key outbound esp simple huawei[CLIGURU-R3-ipsec-policy-manual-P1-10] sa string-key inbound esp simple huawei |
Display IPsec policy komutuyla konfigürasyonu kontrol edelim.
<CLIGURU-R1>display ipsec policy===========================================IPSec policy group: “P1”Using interface:===========================================Sequence number: 10Security data flow: 3001Tunnel local address: 10.0.12.1Tunnel remote address: 10.0.23.3Qos pre-classify: DisableProposal name:tran1Inbound AH setting:AH SPI:AH string-key:AH authentication hex key:Inbound ESP setting:ESP SPI: 12345 (0x3039)ESP string-key: huaweiESP encryption hex key:ESP authentication hex key:Outbound AH setting:AH SPI:AH string-key:AH authentication hex key:Outbound ESP setting:ESP SPI: 54321 (0xd431)ESP string-key: huaweiESP encryption hex key:ESP authentication hex key: |
<CLIGURU-R3>display ipsec policy===========================================IPSec policy group: “P1”Using interface:===========================================Sequence number: 10Security data flow: 3001Tunnel local address: 10.0.23.3Tunnel remote address: 10.0.12.1Qos pre-classify: DisableProposal name:tran1Inbound AH setting:AH SPI:AH string-key:AH authentication hex key:Inbound ESP setting:ESP SPI: 54321 (0xd431)ESP string-key: huaweiESP encryption hex key:ESP authentication hex key:Outbound AH setting:AH SPI:AH string-key:AH authentication hex key:Outbound ESP setting:ESP SPI: 12345 (0x3039)ESP string-key: huaweiESP encryption hex key:ESP authentication hex key: |
6.Interface’lere IPsec Policy uygulamak.
Interfacelerde fiziksel olarak IPsec olusturalm.
[CLIGURU-R1]interface Serial 0/0/1[CLIGURU-R1-Serial0/0/1]ipsec policy P1 |
[CLIGURU-R3]interface Serial 0/0/2[CLIGURU-R3-Serial0/0/2]ipsec policy P1 |
7. Cihazlar arası bağlantıları kontrol edlim.
Cihazlar arası bağlantıları test ettikten sonra IPsec konfigürasyonlarnıda gözlemleyelim.
<CLIGURU-R1>ping -a 10.0.11.11 10.0.33.33PING 10.0.33.33: 56 data bytes, press CTRL_C to breakReply from 10.0.33.33: bytes=56 Sequence=1 ttl=254 time=70 msReply from 10.0.33.33: bytes=56 Sequence=2 ttl=254 time=80 msReply from 10.0.33.33: bytes=56 Sequence=3 ttl=254 time=50 msReply from 10.0.33.33: bytes=56 Sequence=4 ttl=254 time=100 msReply from 10.0.33.33: bytes=56 Sequence=5 ttl=254 time=50 ms— 10.0.33.33 ping statistics —5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 50/70/100 ms |
<CLIGURU-R1>display ipsec statistics espInpacket count : 0Inpacket auth count :0Inpacket decap count : 0Outpacket count :0Outpacket auth count : 0Outpacket encap count : 0Inpacket drop count :0Outpacket drop count : 0BadAuthLen count : 0AuthFail count :0PktDuplicateDrop count : 0PktSeqNoTooSmallDrop count: 0PktInSAMissDrop count : 0 |
Sadece IPsec VPN trafiğini gözlemleyelim.
<CLIGURU-R1>ping -a 10.0.1.1 10.0.3.3PING 10.0.3.3: 56 data bytes, press CTRL_C to breakReply from 10.0.3.3: bytes=56 Sequence=1 ttl=254 time=40 msReply from 10.0.3.3: bytes=56 Sequence=2 ttl=254 time=30 msReply from 10.0.3.3: bytes=56 Sequence=3 ttl=254 time=70 msReply from 10.0.3.3: bytes=56 Sequence=4 ttl=254 time=60 msReply from 10.0.3.3: bytes=56 Sequence=5 ttl=254 time=30 ms— 10.0.3.3 ping statistics —5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 30/46/70 ms |
<CLIGURU-R1>display ipsec statistics espInpacket count : 5Inpacket auth count : 0Inpacket decap count : 0Outpacket count : 5Outpacket auth count : 0Outpacket encap count : 0Inpacket drop count :0Outpacket drop count : 0BadAuthLen count : 0AuthFail count : 0PktDuplicateDrop count : 0PktSeqNoTooSmallDrop count: 0PktInSAMissDrop count : 0 |
8.ACL i yeniden tanımlayalım.
ACL’i OSPF i tanımlatmak için yeniden tanımlıyoruz.
[CLIGURU-R1]acl 3001[CLIGURU-R1-acl-adv-3001]rule 5 permit ospf source any destination any |
[CLIGURU-R3]acl 3001[CLIGURU-R3-acl-adv-3001]rule 5 permit ospf source any destination any |
Komşulukları kotrol ediyoruz.
<CLIGURU-R1>display ospf peer briefOSPF Process 1 with Router ID 10.0.1.1Peer Statistic Information—————————————————————————-Area Id Interface Neighbor id State0.0.0.0 Serial0/0/1 10.0.2.2 Init—————————————————————————- |
<CLIGURU-R1>display ip routing-tableRoute Flags: R – relay, D – download to fib——————————————————————————Routing Tables: PublicDestinations : 13 Routes : 13Destination/Mask Proto Pre Cost Flags NextHop Interface10.0.1.0/24 Direct 0 0 D 10.0.1.1 LoopBack010.0.1.1/32 Direct 0 0 D 127.0.0.1 LoopBack010.0.2.2/32 OSPF 0 0 D 10.0.12.2 Serial0/0/110.0.3.3/32 OSPF 0 0 D 10.0.12.2 Serial0/0/110.0.11.0/24 Direct 0 0 D 10.0.11.11 LoopBack110.0.11.11/32 Direct 0 0 D 127.0.0.1 LoopBack110.0.12.0/24 Direct 0 0 D 10.0.12.1 Serial0/0/110.0.12.1/32 Direct 0 0 D 127.0.0.1 Serial0/0/110.0.12.2/32 Direct 0 0 D 10.0.12.2 Serial0/0/110.0.23.0/24 OSPF 0 0 D 10.0.12.2 Serial0/0/110.0.33.33/32 OSPF 0 0 D 10.0.12.2 Serial0/0/1127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 |
<CLIGURU-R3>display ospf peer briefOSPF Process 1 with Router ID 10.0.3.3Peer Statistic Information—————————————————————————-Area Id Interface Neighbor id State0.0.0.0 Serial0/0/2 10.0.2.2 Init—————————————————————————- |
<CLIGURU-R3>display ip routing-tableRoute Flags: R – relay, D – download to fib——————————————————————————Routing Tables: PublicDestinations : 13 Routes : 13Destination/Mask Proto Pre Cost Flags NextHop Interface10.0.1.1/32 OSPF 0 0 D 10.0.23.2 Serial0/0/210.0.2.2/32 OSPF 0 0 D 10.0.23.2 Serial0/0/210.0.3.0/24 Direct 0 0 D 10.0.3.3 LoopBack010.0.3.3/32 Direct 0 0 D 127.0.0.1 LoopBack010.0.11.11/32 OSPF 0 0 D 10.0.23.2 Serial0/0/210.0.12.0/24 OSPF 0 0 D 10.0.23.2 Serial0/0/210.0.23.0/24 Direct 0 0 D 10.0.23.3 Serial0/0/210.0.23.2/32 Direct 0 0 D 10.0.23.2 Serial0/0/210.0.23.3/32 Direct 0 0 D 127.0.0.1 Serial0/0/210.0.33.0/24 Direct 0 0 D 10.0.33.33 LoopBack110.0.33.33/32 Direct 0 0 D 127.0.0.1 LoopBack1127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 |
Sonuç…..
<CLIGURU-R2>dis current-configuration#sysname CLIGURU-R2#interface Serial0/0/1link-protocol pppip address 10.0.12.2 255.255.255.0#interface Serial0/0/2link-protocol pppip address 10.0.23.2 255.255.255.0#interface LoopBack0ip address 10.0.2.2 255.255.255.0#ospf 1 router-id 10.0.2.2area 0.0.0.0network 10.0.2.0 0.0.0.255network 10.0.12.0 0.0.0.255network 10.0.23.0 0.0.0.255#user-interface con 0user-interface vty 0 4user-interface vty 16 20#Return |
<CLIGURU-R3>display current-configuration#sysname CLIGURU-R3#acl number 3001rule 5 permit ospf#ipsec proposal tran1esp authentication-algorithm sha1esp encryption-algorithm 3des#ipsec policy P1 10 manualsecurity acl 3001proposal tran1tunnel local 3.23.0.10tunnel remote 1.12.0.10sa spi inbound esp 835977216sa string-key inbound esp simple huaweisa spi outbound esp 959447040sa string-key outbound esp simple huawei#interface Serial0/0/2link-protocol pppip address 10.0.23.3 255.255.255.0ipsec policy P1#interface LoopBack0ip address 10.0.3.3 255.255.255.0#interface LoopBack1ip address 10.0.33.33 255.255.255.0#ospf 1 router-id 10.0.3.3area 0.0.0.0network 10.0.23.0 0.0.0.255network 10.0.3.0 0.0.0.255network 10.0.33.0 0.0.0.255#user-interface con 0user-interface vty 0 4user-interface vty 16 20#return |