-
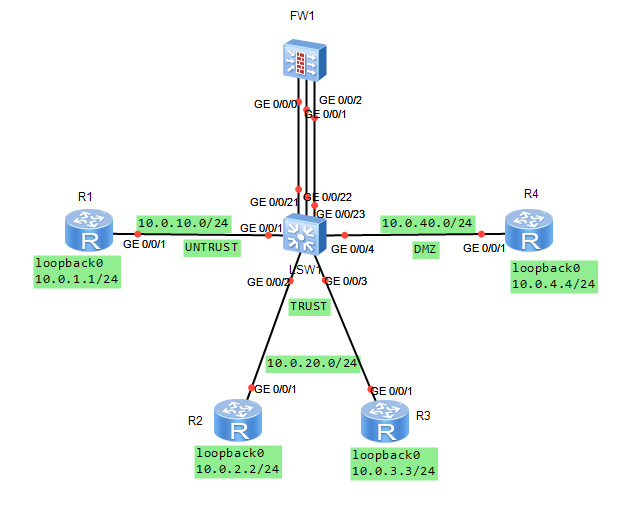
Cihaz ip address yapılandırması.
<Huawei>system-viewEnter system view, return user view with Ctrl+Z.[Huawei]sysname R1[R1]interface GigabitEthernet 0/0/1[R1-GigabitEthernet0/0/1]ip address 1.1.1.1 24[R1-GigabitEthernet0/0/1]interface loopback 0[R1-LoopBack0]ip address 10.0.1.1 24 |
<Huawei>system-viewEnter system view, return user view with Ctrl+Z.[Huawei]sysname R2[R2]interface GigabitEthernet0/0/1[R2-GigabitEthernet0/0/1]ip address 10.0.20.2 24[R2-GigabitEthernet0/0/1]interface loopback 0[R2-LoopBack0]ip address 10.0.2.2 24 |
<Huawei>system-viewEnter system view, return user view with Ctrl+Z.[Huawei]sysname R3[R3]interface GigabitEthernet0/0/1[R3-GigabitEthernet0/0/1]ip address 10.0.20.3 24[R3-GigabitEthernet0/0/1]interface loopback 0[R3-LoopBack0]ip address 10.0.3.3 24 |
<Huawei>system-viewEnter system view, return user view with Ctrl+Z.[Huawei]sysname R4[R4]interface GigabitEthernet 0/0/1[R4-GigabitEthernet0/0/1]ip address 10.0.40.4 24[R4-GigabitEthernet0/0/1]interface loopback 0[R4-LoopBack0]ip address 10.0.4.4 24 |
Firewall üzerinde layer 2 ,switch interface ve ip address konfigürasyonu yapılmaz.
Lab’da, firewall üzerinde VLAN 12 oluşturalım ve VLANIF 12 interfacesini oluşturalım. Trust bölgede network gatewayının IP adresi olarak VLANIF 12 interface IP adresini yapılandıralım ve 10.0.20.254/24 IP adresini ayarlayalım.
<Eudemon 200E>system-viewEnter system view, return user view with Ctrl+Z.[Eudemon 200E]sysname FW[FW]vlan 12[FW-vlan-12]quit[FW]interface Vlanif 12[FW-Vlanif12]ip address 10.0.20.254 24[FW-Vlanif12]interface ethernet 1/0/0[FW-Ethernet1/0/0]port access vlan 12[FW-Ethernet1/0/0]undo interface Vlanif 1[FW]interface Ethernet 0/0/0[FW-Ethernet0/0/0]ip address 1.1.1.254 24[FW-Ethernet0/0/0]interface ethernet 2/0/0[FW-Ethernet2/0/0]ip address 10.0.40.254 24 |
Cihazın G0/0/1 ve G0/0/24 interfacelerine VLAN 11 i ekleyelim.
Cihazın G0/0/2 , G0/0/3 ve G0/0/22 interfacelerine VLAN 12 i ekleyelim.
Cihazın G0/0/4 ve G0/0/23 interfacelerine VLAN 13ü ekleyelim.
[Quidway]sysname S1[S1]vlan batch 11 to 13[S1]interface GigabitEthernet 0/0/1[S1-GigabitEthernet0/0/1]port link-type access[S1-GigabitEthernet0/0/1]port default vlan 11[S1-GigabitEthernet0/0/1]interface GigabitEthernet 0/0/2[S1-GigabitEthernet0/0/2]port link-type access[S1-GigabitEthernet0/0/2]port default vlan 12[S1-GigabitEthernet0/0/2]interface GigabitEthernet 0/0/3[S1-GigabitEthernet0/0/3]port link-type access[S1-GigabitEthernet0/0/3]port default vlan 12[S1-GigabitEthernet0/0/2]interface GigabitEthernet 0/0/4[S1-GigabitEthernet0/0/3]port link-type access[S1-GigabitEthernet0/0/3]port default vlan 13[S1-GigabitEthernet0/0/3]interface GigabitEthernet 0/0/21[S1-GigabitEthernet0/0/21]port link-type access[S1-GigabitEthernet0/0/21]port default vlan 11[S1-GigabitEthernet0/0/21]interface GigabitEthernet 0/0/22[S1-GigabitEthernet0/0/22]port link-type access[S1-GigabitEthernet0/0/22]port default vlan 12[S1-GigabitEthernet0/0/22]interface GigabitEthernet 0/0/23[S1-GigabitEthernet0/0/23]port link-type access[S1-GigabitEthernet0/0/23]port default vlan 13 |
-
Network iletişimi için static routei yapılandıralım.
[R2]ip route-static 0.0.0.0 0 10.0.20.254 |
[R3]ip route-static 0.0.0.0 0 10.0.20.254 |
[R4]ip route-static 0.0.0.0 0 10.0.40.254 |
[FW]ip route-static 10.0.2.0 24 10.0.20.2[FW]ip route-static 10.0.3.0 24 10.0.20.3[FW]ip route-static 10.0.4.0 24 10.0.40.4[FW]ip route-static 0.0.0.0 0 1.1.1.1 |
Bağlantıları kontrol edelim.
[FW]ping 10.0.1.1PING 10.0.1.1: 56 data bytes, press CTRL_C to breakReply from 10.0.1.1: bytes=56 Sequence=1 ttl=255 time=1 msReply from 10.0.1.1: bytes=56 Sequence=2 ttl=255 time=1 msReply from 10.0.1.1: bytes=56 Sequence=3 ttl=255 time=1 msReply from 10.0.1.1: bytes=56 Sequence=4 ttl=255 time=1 msReply from 10.0.1.1: bytes=56 Sequence=5 ttl=255 time=1 ms— 10.0.1.1 ping statistics —5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 1/1/1 ms |
[FW]ping 10.0.2.2PING 10.0.2.2: 56 data bytes, press CTRL_C to breakReply from 10.0.2.2: bytes=56 Sequence=1 ttl=255 time=1 msReply from 10.0.2.2: bytes=56 Sequence=2 ttl=255 time=1 msReply from 10.0.2.2: bytes=56 Sequence=3 ttl=255 time=1 msReply from 10.0.2.2: bytes=56 Sequence=4 ttl=255 time=1 msReply from 10.0.2.2: bytes=56 Sequence=5 ttl=255 time=1 ms— 10.0.2.2 ping statistics —5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 1/1/1 ms |
[FW]ping 10.0.3.3PING 10.0.3.3: 56 data bytes, press CTRL_C to breakReply from 10.0.3.3: bytes=56 Sequence=1 ttl=255 time=1 msReply from 10.0.3.3: bytes=56 Sequence=2 ttl=255 time=1 msReply from 10.0.3.3: bytes=56 Sequence=3 ttl=255 time=1 msReply from 10.0.3.3: bytes=56 Sequence=4 ttl=255 time=1 msReply from 10.0.3.3: bytes=56 Sequence=5 ttl=255 time=1 ms— 10.0.3.3 ping statistics —5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 1/1/1 ms |
[FW]ping 10.0.4.4PING 10.0.4.4: 56 data bytes, press CTRL_C to breakReply from 10.0.4.4: bytes=56 Sequence=1 ttl=255 time=1 msReply from 10.0.4.4: bytes=56 Sequence=2 ttl=255 time=1 msReply from 10.0.4.4: bytes=56 Sequence=3 ttl=255 time=1 msReply from 10.0.4.4: bytes=56 Sequence=4 ttl=255 time=1 msReply from 10.0.4.4: bytes=56 Sequence=5 ttl=255 time=1 ms— 10.0.4.4 ping statistics —5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 1/1/1 ms |
-
Security i interfacelerde etkinleştirme .
Default olarak firewallda 4 bölge oluşturulur . Bunlar local, trusted, untrusted ve DMZ bölgeleridir.
Bu labda , trusted, untrusted ve DMZ bölgelerini kullanılır.
[FW]firewall zone dmz[FW-zone-dmz]add interface Ethernet 2/0/0[FW-zone-dmz]firewall zone trust[FW-zone-trust]add interface Vlanif 12[FW-zone-trust]firewall zone untrust[FW-zone-untrust]add interface Ethernet 0/0/0 |
Default olarak, tüm bölgeler arasında iletişim normaldir. NAT etkin değil; Bu nedenle, dış bölgeleri, iç bölgeleri ve DMZ bölgesi ile iletişim kurulamıyor.
-
Bölgeler arasındaki security filtreleme yapılandırması.
Paketleri 10.0.2.0 ve 10.0.3.0 netwoklerinden iletmek için Untrust bölgeye trust bölgeyi yapılandıralım. Untrust bölgeden DMZ bölgesine Telnet ve FTP isteği paketleri 10.0.4.4 ağ netwoku üzerinden geçmesi için yapılandıralım.
[FW]firewall session link-state check[FW]policy interzone trust untrust outbound[FW-policy-interzone-trust-untrust-outbound]policy 0[FW-policy-interzone-trust-untrust-outbound-0]policy source 10.0.2.0 0.0.0.255[FW-policy-interzone-trust-untrust-outbound-0]policy source 10.0.3.0 0.0.0.255[FW-policy-interzone-trust-untrust-outbound-0]action permit[FW-policy-interzone-trust-untrust-outbound-0]quit[FW-policy-interzone-trust-untrust-outbound]quit[FW]policy interzone dmz untrust inbound[FW-policy-interzone-dmz-untrust-inbound]policy 0[FW-policy-interzone-dmz-untrust-inbound-0]policy destination 10.0.4.4 0[FW-policy-interzone-dmz-untrust-inbound-0]policy service service-set telnet[FW-policy-interzone-dmz-untrust-inbound-0]policy service service-set ftp[FW-policy-interzone-dmz-untrust-inbound-0]action permit[FW-policy-interzone-dmz-untrust-inbound-0]quit |
-
NAT ip address yapılandırması.
Addff
[FW]nat-policy interzone trust untrust outbound[FW-nat-policy-interzone-trust-untrust-outbound]policy 0[FW-nat-policy-interzone-trust-untrust-outbound-0]policy source 10.0.2.0 0.0.0.255[FW-nat-policy-interzone-trust-untrust-outbound-0]action source-nat[FW-nat-policy-interzone-trust-untrust-outbound-0]easy-ip Ethernet 0/0/0 |
Konfigürasyonu kontrol edelim.
[R2]ping 10.0.1.1PING 10.0.1.1: 56 data bytes, press CTRL_C to breakRequest time outRequest time outRequest time outRequest time outRequest time out— 10.0.1.1 ping statistics —5 packet(s) transmitted0 packet(s) received100.00% packet loss |
[R2]ping -a 10.0.2.2 10.0.1.1PING 10.0.1.1: 56 data bytes, press CTRL_C to breakReply from 10.0.1.1: bytes=56 Sequence=1 ttl=254 time=4 msReply from 10.0.1.1: bytes=56 Sequence=2 ttl=254 time=3 msReply from 10.0.1.1: bytes=56 Sequence=3 ttl=254 time=3 msReply from 10.0.1.1: bytes=56 Sequence=4 ttl=254 time=3 msReply from 10.0.1.1: bytes=56 Sequence=5 ttl=254 time=3 ms— 10.0.1.1 ping statistics —5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 3/3/4 ms |
Doğrudan R2 den 10.0.1.1 ping varsa, ping başarısız olur. Extended ping kullanın. Bir kaynak IP adresi 10.0.2.2 olarak belirtildikten sonra, ping başarılı olacaktıır.
Paketin bu kaynak IP adresi NAT adres aralığında olmadığı, 10.0.20.2 olmasıdır.
[FW]display nat-policy interzone trust untrust outbound10:46:37 2011/12/26nat-policy interzone trust untrust outboundpolicy 0 (1 times matched)action source-natpolicy service service-set ippolicy source 10.0.2.0 0.0.0.255policy destination anyeasy-ip Ethernet0/0/0 |
-
Bir adres grubu yapılandırması
Kaynak IP adresine tercüme ve adres grubuna NAT politikasına bağlamak için bir adres grubunu yapılandıralım.
[FW]nat address-group 1 1.1.1.3 1.1.1.10[FW]nat-policy interzone trust untrust outbound[FW-nat-policy-interzone-trust-untrust-outbound]policy 1[FW-nat-policy-interzone-trust-untrust-outbound-0]policy source 10.0.3.0 0.0.0.255[FW-nat-policy-interzone-trust-untrust-outbound-0]action source-nat[FW-nat-policy-interzone-trust-untrust-outbound-0]address-group 1 |
Trust ve untrust bölgeleri kontrol edelim.
[R3]ping -a 10.0.3.3 10.0.1.1PING 10.0.1.1: 56 data bytes, press CTRL_C to breakReply from 10.0.1.1: bytes=56 Sequence=1 ttl=254 time=12 msReply from 10.0.1.1: bytes=56 Sequence=2 ttl=254 time=3 msReply from 10.0.1.1: bytes=56 Sequence=3 ttl=254 time=4 msReply from 10.0.1.1: bytes=56 Sequence=4 ttl=254 time=2 msReply from 10.0.1.1: bytes=56 Sequence=5 ttl=254 time=3 ms— 10.0.1.1 ping statistics —5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 2/4/12 ms |
Extended ping kullanın. Bir kaynak IP adresi 10.0.3.3 olarak belirtildikten sonra, ping başarılı.
[FW]display nat-policy interzone trust untrust outbound10:52:37 2011/12/26nat-policy interzone trust untrust outboundpolicy 0 (2 times matched)action source-natpolicy service service-set ippolicy source 10.0.2.0 0.0.0.255policy destination anyeasy-ip Ethernet0/0/0policy 1 (0 times matched)action source-natpolicy service service-set ippolicy source 10.0.3.0 0.0.0.255policy destination anyaddress-group 1 |
Trust bölgeden IP adresi 10.0.2.0/24 ve 10.0.3.0/24 untrust bölgeye erişebilirsiniz.
-
0.4.4 IP adresi ile intranet sunucu tarafından sağlanan hizmetlerin reklamı yapılandırması.
Map Telnet ve FTP servis için 10.0.4.4 ve 1.1.1.100 ettkinleştirelim.
[FW]nat server protocol tcp global 1.1.1.100 telnet inside 10.0.4.4 telnet[FW]nat server protocol tcp global 1.1.1.100 ftp inside 10.0.4.4 ftp |
Final Configurations
[FW]display current-configuration#sysname FW#nat address-group 1 1.1.1.3 1.1.1.10nat server 0 protocol tcp global 1.1.1.100 telnet inside 10.0.4.4 telnetnat server 1 protocol tcp global 1.1.1.100 ftp inside 10.0.4.4 ftpnat server 2 protocol tcp global 1.1.1.200 telnet inside 10.0.3.3 telnet#vlan batch 1 12#firewall session link-state check#interface Vlanif12ip address 10.0.20.254 255.255.255.0#interface Ethernet0/0/0ip address 1.1.1.254 255.255.255.0#interface Ethernet1/0/0portswitchport link-type accessport access vlan 12#interface Ethernet2/0/0ip address 10.0.40.254 255.255.255.0#firewall zone trustset priority 85add interface Vlanif12#firewall zone untrustset priority 5add interface Ethernet0/0/0#firewall zone dmzset priority 50add interface Ethernet2/0/0#firewall interzone dmz untrustdetect ftp#ip route-static 0.0.0.0 0.0.0.0 1.1.1.1ip route-static 10.0.2.0 255.255.255.0 10.0.20.2ip route-static 10.0.3.0 255.255.255.0 10.0.20.3ip route-static 10.0.4.0 255.255.255.0 10.0.40.4#policy interzone trust untrust outboundpolicy 0action permitpolicy source 10.0.2.0 0.0.0.255policy source 10.0.3.0 0.0.0.255#policy interzone dmz untrust inboundpolicy 0action permitpolicy service service-set ftppolicy service service-set telnetpolicy destination 10.0.4.4 0#nat-policy interzone trust untrust outboundpolicy 0action source-natpolicy source 10.0.2.0 0.0.0.255easy-ip Ethernet0/0/0policy 1action source-natpolicy source 10.0.3.0 0.0.0.255address-group 1#nat-policy zone trustpolicy 0action source-natpolicy source 10.0.2.0 0.0.0.255policy destination 1.1.1.200 0address-group 1#Return |
<R1>display current-configuration[V200R001C00SPC200]#sysname R1##interface GigabitEthernet0/0/1ip address 1.1.1.1 255.255.255.0#interface LoopBack0ip address 10.0.1.1 255.255.255.0#Return<R2>display current-configuration[V200R001C00SPC200]#sysname R2#interface GigabitEthernet0/0/1ip address 10.0.20.2 255.255.255.0#interface LoopBack0ip address 10.0.2.2 255.255.255.0#ip route-static 0.0.0.0 0.0.0.0 10.0.20.254#Return[R3]display current-configuration[V200R001C00SPC200]#sysname R3#interface GigabitEthernet0/0/1ip address 10.0.20.3 255.255.255.0#interface LoopBack0ip address 10.0.3.3 255.255.255.0#ip route-static 0.0.0.0 0.0.0.0 10.0.20.254#user-interface vty 0 4authentication-mode none#Return |
[R4]display current-configuration[V200R001C00SPC500]#sysname R4ftp server enable##aaalocal-user huawei password simple huaweilocal-user huawei ftp-directory flash:local-user huawei service-type ftp#interface GigabitEthernet0/0/1ip address 10.0.40.4 255.255.255.0#interface LoopBack0ip address 10.0.4.4 255.255.255.0#ip route-static 0.0.0.0 0.0.0.0 10.0.40.254#user-interface vty 0 4authentication-mode none#Return |
<S1>display current-configuration#!Software Version V100R006C00SPC800sysname S1#vlan batch 11 to 13#interface GigabitEthernet0/0/1port link-type accessport default vlan 11#interface GigabitEthernet0/0/2port link-type accessport default vlan 12#interface GigabitEthernet0/0/3port link-type accessport default vlan 12#interface GigabitEthernet0/0/4port link-type accessport default vlan 13#interface GigabitEthernet0/0/21port link-type accessport default vlan 11#interface GigabitEthernet0/0/22port link-type accessport default vlan 12#interface GigabitEthernet0/0/23port link-type accessport default vlan 13#return |